March 25, 2022
The Intelligence Cycle: Generating OSINT from OSINF

Steve Adams
Product Marketing Manager
The Intelligence Cycle is a structured process that outlines the steps involved in producing intelligence. Intelligence, most simply defined as information with added value, is the output of the intelligence cycle, where raw data and information flow into the process and emerge with value for the organization.
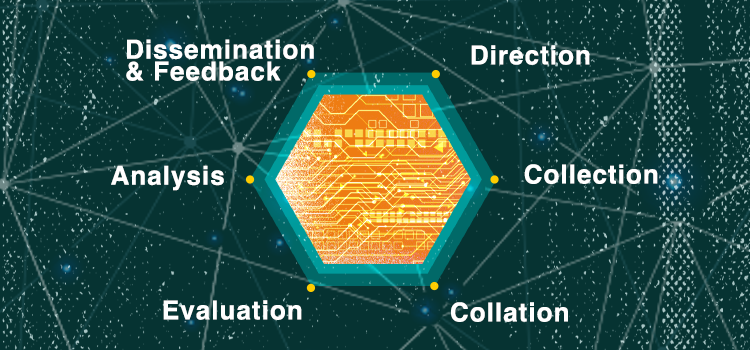
There are a variety of conceptualizations of the Intelligence Cycle, which range between four and seven steps. Each conceptualization outlines the same process and simply groups stages into a different visualization. These steps can include:
- Direction
- Collection
- Collation
- Evaluation (Sometimes grouped with Analysis under Processing)
- Analysis
- Dissemination and Feedback
When conducting investigative internet activity, the intelligence cycle should play a part in the process. The intelligence cycle creates open-source intelligence (OSINT) from open-source information (OSINF) and ensures dissemination to decision-makers.
Direction
During the first step in the intelligence cycle, Direction, the intelligence requirement is determined, and a plan to collect data or information is specified.
To identify an intelligence requirement, an intelligence analyst receives a request for or discerns the need for an intelligence product.
A request for intelligence or a product can be more informal, made over email or a phone call, or could come in through a formal process. Analysts must summarize the intelligence requirements with the requestor and get them to sign off on the request, ensuring that any misunderstandings are clarified.
At the direction stage, the analyst gets an idea of the problem they must solve and creates an Intelligence Collection Plan. An Intelligence Collection Plan outlines the intelligence requirements to ensure the information gathered works towards a clear purpose, summarizing the planned collection efforts and listing priorities for the intelligence product.
Producing a written intelligence collection plan enables the analyst to identify any problem areas that they may miss with a less formal process.
During an internet investigation, the investigator or analyst should outline the information required, which sources they intend to probe, and the extraction method. With new social media platforms and communication applications emerging, it is vital to keep on top of the sources that need searching during manual investigations. When utilizing an investigation automation tool like Skopenow, a collection plan should identify the intended search terms.
Collection
With the intelligence requirements outlined in the Intelligence Collection plan, the Collection stage can begin.
The Collection stage follows the Intelligence Collection Plan to ensure relevant, accurate, and valuable information that impacts decision-making.
Internet information collection can involve a variety of sources, which may include:
- Consented Data and Telephone Directories
- Social Media Platforms
- Web Articles, Newspapers, Magazines, Newsletters, and Journal Articles.
- Court Records
- Motor Vehicle Registration and Insurance Records
- Land Deeds and Planning Permission
- Mapping Solutions
- Data Breach Sources
- The Dark Web
- Digital Marketplaces
- Public Demographic Data
- Sex Offender Registries
Collation
The third stage of the intelligence cycle, Collation, refers to the sorting, organizing, categorizing, and indexing of the collected data. During the collation stage, related information is grouped to outline and corroborate a record of events.
If audio and video records are archived during an internet investigation, they may require transcription and potentially translation. The collation process ensures that investigators or analysts involved in the intelligence cycle can locate, review, and group the collected information.
Evaluation
During the Evaluation stage, the analyst reviews the organized information, which should not be taken at face value. For each piece of information, the Evaluation stage assesses its validity and the source's reliability. For this process, an intelligence grading process, such as the 3x5x2 system, is commonly employed to evaluate information.
Source Evaluation
Source evaluation assesses the credibility of the information source. Under the 3x5x2 system, there are three source gradings:
- Reliable – The source is understood to be competent and well tested, with information previously received from them being generally reliable. Reliable information can likely be trusted and relied on.
- Untested – The source has not previously provided information or has provided information that is not yet substantiated, so their reliability cannot be judged. Untested information should be treated with caution and corroborated before being acted upon.
- Not reliable – There are reasonable grounds to doubt the reliability of the source due to previously providing inaccurate information, or an ulterior motive exists. Corroborative evidence should be sought before making decisions on this information.
With any information collected from the internet, source evaluation scrutinizes the website the information originated from. Consented PII from a government database is generally reliable, whilst posts on an alt-right social media platform from an untested source should not be as trusted.
Information Assessment
Information assessment describes the reliability of the information collected. Under the 3x5x2 system, there are five information assessment gradings:
- Known directly to the source – Information obtained first-hand by the source, usually a direct witness.
- Known indirectly to the source but corroborated – Information that the source has not witnessed themselves, however, the information can be supported by another source assessed as A.
- Known indirectly to the source – Information that the source has heard from someone else.
- Not known – There is no way to assess the information, such as because it originated from an anonymous source.
- Suspected to be false – Information where there is a reason to believe it to be false.
With any information collected from the internet, information assessment looks at the information source. If information is posted by the subject or is from a government database, then the reliability is Known directly to the source. If the information is from a tweet from an unknown person, then the reliability is likely to be Not known.
Information Classification
During the evaluation stage, information is commonly classified for its level of sensitivity. There are typically four information evaluation gradings:
- Unclassified - Publicly available information without the need for any restriction. Distribution may be limited through Freedom of Information requests.
- Official/ Confidential - Information where disclosure or loss could cause damage to the organization or national security.
- Secret - Information where unauthorized disclosure could cause serious damage to the national security or the organization. Secret information could relate to military capabilities, international relations, or ongoing investigations into serious organized crime.
- Top Secret - Information where unauthorized disclosure could cause exceptionally grave damage to the national security or the organization. Top Secret information would include any particulars where divulgence would result in widespread loss of life or threaten the security or economic wellbeing of the country or friendly nations.
Information collected from the internet is generally collected as publicly available information, however, when grouped with internal data and information it can end up being classified at any classification level.
Analysis
The Analysis stage takes place once information has been collected, processed, and evaluated. The analysis stage involves amalgamating information to identify patterns, trends, and inconsistencies. Analyzing information enables analysts to draw inferences and produce actionable intelligence for decision-makers to rely on during operations to prevent or disrupt incidents or apprehend individuals.
The Analysis stage delivers contextual insights to inform analytical deductions and outline the significance of the information. Recognizing the importance of information means understanding what is happening, why it is happening, how it relates to what is already known, why it is relevant, and what could happen next.
Once the analysis has taken place, the analyst produces SMART outcome-focused recommendations based on the findings. Recommendations within intelligence products focus on the operational activity required to disrupt or apprehend offenders.
SMART recommendations should consider:
- the required outcome
- the potential short, medium, and long-term benefits of the possible responses
- the potential risks of the possible responses
- the cost of the possible responses
- the cost-effectiveness of the possible responses
During an internet investigation, the analysis stage may identify trends in the information, such as existing relationships between subjects, specific behaviors, or trends in language that denote code. Recommendations within an OSINT product may include conducting surveillance on or arresting subjects.
Dissemination and Feedback
The final stage of the intelligence cycle, Dissemination and Feedback, is the timely delivery of intelligence to those who need it and review of the final product. Dissemination ensures that the produced intelligence product reaches the decision-makers in the required format.
Intelligence must be disseminated appropriately for the audience, highlighting the key facts and recommendations. Intelligence products can be short summaries, lengthy reports, geospatial maps, oral briefings, or formal presentations. The intelligence analyst will produce the results of their analysis and their recommendations in the format that best suits the intended audience.
During the Dissemination stage, the analyst determines who should receive an intelligence product and what form of product they should receive. An analyst may need to produce several product formats to suit different audiences, such as a full report for an investigator but a summary for executives.
During an internet investigation, products generally take the form of subject profiles or business profiles; intelligence reports that outline information on a person or business. Internet investigations can also inform problem profiles on emerging issues, such as geopolitical issues.
Once a product has been disseminated, feedback evaluates the shared intelligence products and reviews whether it satisfied the initial request. Seeking assessment from the audience, an analyst can utilize the response to inform, adjust, and optimize future products.
Skopenow augments investigations by instantly building comprehensive, court-ready, digital reports on businesses and individuals. Skopenow collects, collates, and analyzes information from data sources including social media, the dark web, associated vehicles, court records, and contact data. Sign up for a 7-day free trial of Skopenow at: https://www.skopenow.com/try.